Last Updated on 9 February 2024 by Alastair Digby
Effective vulnerability management in the modern threat landscape is cyclical. Faced with a dynamic and expanding attack surface, new vulnerabilities constantly emerge in the complex interplay between people and technology. It’s not enough to just find vulnerabilities at a point in time, fix them, and then consider vulnerability management “done”. This article overviews the vulnerability management lifecycle and describes its importance for strengthening your company’s security posture.
Table of Contents
What is a Vulnerability?
A vulnerability is a flaw in a computer system that weakens its security and can be exploited by a malicious actor for nefarious purposes. A crucial part of this definition is that vulnerabilities don’t just come from weaknesses in the design or implementation of software or hardware; how a system is operated or managed can also result in vulnerabilities.
IT security vulnerabilities have been around since well before the invention of modern personal computers. In 1965, William D. Mathews from MIT found a vulnerability in an operating system running on an IBM mainframe computer. This vulnerability revealed the contents of the operating system’s password file to any user when multiple versions of the system’s text editor were opened simultaneously.
During the 1990s, as personal computing became mainstream, and businesses started using a wider variety of software applications, more security vulnerabilities emerged. Various vendors released the earliest vulnerability scanners to help security professionals identify vulnerabilities. However, the problem was that each vendor used its own database of vulnerabilities, which created headaches for security professionals trying to verify scan results and cross-reference different databases.
In 1999, the idea came to fruition that a list of Common Vulnerabilities and Exposures (CVE) would be much more useful and remove confusion by negating any need for cross-referencing across databases. The first-ever CVE list contained 321 publicly known vulnerabilities—the most recent count stands at 196,196, with 18,378 reported in 2021 alone.
Aside from known CVE vulnerabilities for which patches and fixes exist, there is also the constantly lurking threat of zero-day vulnerabilities. These are vulnerabilities for which no patch or other mitigation is yet available.
Common Security Vulnerabilities
The non-profit organisation the Open Worldwide Application Security Project (OWASP) has for decades been striving to help improve the security of software. The OWASP Top 10 provides development teams with a list of top web security vulnerabilities based on data from the security community. Below we’ve listed the current OWASP Top 10:
- SQL Injection
- Cross Site Scripting
- Broken Authentication and Session Management
- Insecure Direct Object References
- Cross Site Request Forgery
- Security Misconfiguration
- Insecure Cryptographic Storage
- Failure to restrict URL Access
- Insufficient Transport Layer Protection
- Unvalidated Redirects and Forwards
The 6 steps in the Vulnerability Management Lifecycle
The following diagram illustrates the 6 steps in the vulnerability management lifecycle.
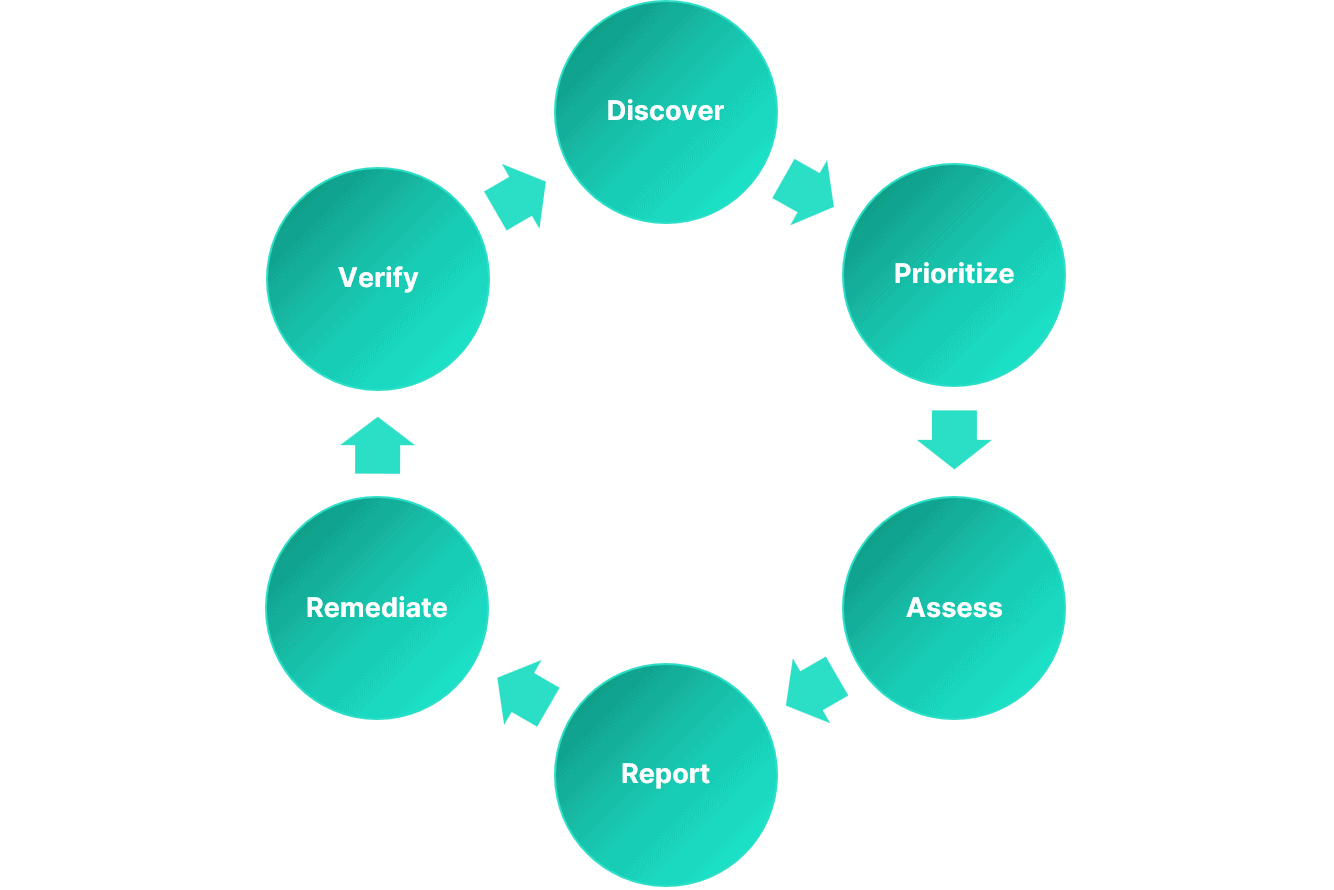
The point of the vulnerability management lifecycle is to put in place a systematic approach that enables organizations to discover vulnerabilities in their IT environment, understand their risks, and remediate them.
The importance of a cyclical and continuous approach to the vulnerability management lifecycle is reflected in the 7th Critical Security Control devised by the Center for Internet Security. According to the advice, organizations should, “develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and minimize, the window of opportunity for attackers.” A solid basis for this plan comes from the vulnerability management lifecycle.
Discover
The first stage in the vulnerability management lifecycle is an effort to discover and create an inventory of all the different assets that should be scanned for vulnerabilities (e.g. software, web apps, operating systems, devices). Comprehensive discovery is critical in avoiding situations where you have vulnerabilities in systems or apps that aren’t properly tracked.
Useful tools to help account for all assets include network scanners, cloud management consoles, and dedicated asset discovery platforms that can even find unknown or shadow IT assets. The iterative nature of the lifecycle means that once an inventory is established, the discovery stage of future vulnerability management cycles can refine or update your existing inventory.
Prioritize Assets
Since not every asset carries the same level of importance for businesses, it’s important to group systems by their priority. Typical characteristics of high-priority assets are those that are central to normal business operations, that lack fault tolerance, or that store sensitive data.
The point here is that since vulnerability management programs are often constrained by limitations in personnel or other resources, it’s prudent to focus on hunting down vulnerabilities in high-priority assets first. When neglected and left vulnerable, organizations face significantly higher risks from potential compromises of high-impact systems. Lower priority assets don’t get ignored in vulnerability assessments, but they do take a back seat.
Assess
The assessment stage is where you run traditional vulnerability scans, ideally using as much automation as possible. You should aim for both breadth and depth here. Breadth comes from deploying dedicated tools that scan web apps, cloud infrastructure, and all other assets in your inventory for code vulnerabilities, misconfigurations, etc. You can achieve depth by adding penetration testing to the mix, in which expert security testers probe for vulnerabilities that are difficult to detect with scanning tools.
After enumerating vulnerabilities, it’s important to combine this information with your prioritized list of assets and other contextual information. This contextual information includes a risk rating for the vulnerability and the exposure level of the impacted asset(s). All of this information sets the groundwork for accurate and informative reporting on vulnerabilities and how to prioritize them for remediation.
Report
It’s critical to compile the data gathered during previous steps and present this information to relevant stakeholders in the form of documented findings. Reports should be tailored to different audiences based on their need for technical details. Executives and other technology decision-makers require high-level trends communicated concisely. Security teams need clear and detailed reports that facilitate smooth remediation efforts, ideally with recommended fixes outlined.
Remediate
The remediation phase includes any action to fix a vulnerability, whether that means applying a security patch, updating hardware, or changing system configurations. Sometimes, direct remediation is not immediately possible, so the best course of action will be to mitigate the risk of a vulnerability being exploited until a fix is practical, for example, by isolating a vulnerable system from the rest of the network. The severity of a vulnerability and the criticality of the underlying system will help to prioritize remediation.
Verify
The verification phase completes the vulnerability management lifecycle by double-checking that any attempts to remove or mitigate vulnerabilities have been successful. The verification phase can overlap with the discover and assess phases of the next cycle because organizations need to regularly scan and assess their IT environments for vulnerabilities. Alternatively, follow-up audits involving separate re-scans or penetration tests can help to verify if remediation actions were successful.
The Importance of the Vulnerability Management Lifecycle
The importance of the vulnerability management lifecycle is how it conveys the need for an iterative and ongoing approach to managing vulnerabilities. Results and reports from each cycle of vulnerability management should inform the next cycle, for example, by highlighting key performance indicators where your business isn’t hitting its objectives.
Additionally, verifying that vulnerabilities were successfully mitigated helps to reduce the attack surface of systems. With fewer weaknesses to exploit, your company’s security posture strengthens. And, the next cycle of vulnerability management (hopefully) comes with fewer vulnerabilities to discover and remediate.
Vulnerability Management Informs Attack Surface Management
While vulnerability management does help to reduce your attack surface, a dedicated approach to attack surface management encompasses visibility into all external assets and the discovery of all potential entry points across infrastructure, devices, apps, and data. Attack surface management also accounts for the interconnectedness of different systems and components for more granular risk management.
Informer’s external attack surface management platform provides automated asset and vulnerability discovery, with integrated penetration testing able to unearth more complex vulnerabilities that typical scans may not find. You also get actionable security insights for uncovering new risks and helping to shrink your attack surface.
Frequently Asked Questions
How can organizations identify vulnerabilities?
Organizations can identify vulnerabilities through various methods, including:
Vulnerability scanning: Using automated tools to scan systems and networks for known vulnerabilities.
Penetration testing: Conducting controlled tests to simulate real-world attacks and identify vulnerabilities.
Monitoring security advisories: Staying informed about security vulnerabilities and patches released by software vendors, security organizations, and industry sources.
How are vulnerabilities assessed and prioritized?
Vulnerabilities are assessed and prioritized based on factors such as their severity, potential impact on the organization, exploitability, and the value of the affected assets.
Common methods include using vulnerability scoring systems, such as the Common Vulnerability Scoring System (CVSS), and considering additional contextual factors specific to the organization’s environment.
How can organizations ensure the effectiveness of vulnerability management?
Organizations can ensure the effectiveness of vulnerability management by:
Establishing clear policies and procedures for vulnerability management.
Automating vulnerability scanning and assessment processes.
Regularly reviewing and updating vulnerability management practices based on industry best practices.
Conducting periodic audits and assessments of the vulnerability management program.
Promoting a culture of security awareness and proactive risk management within the organization.