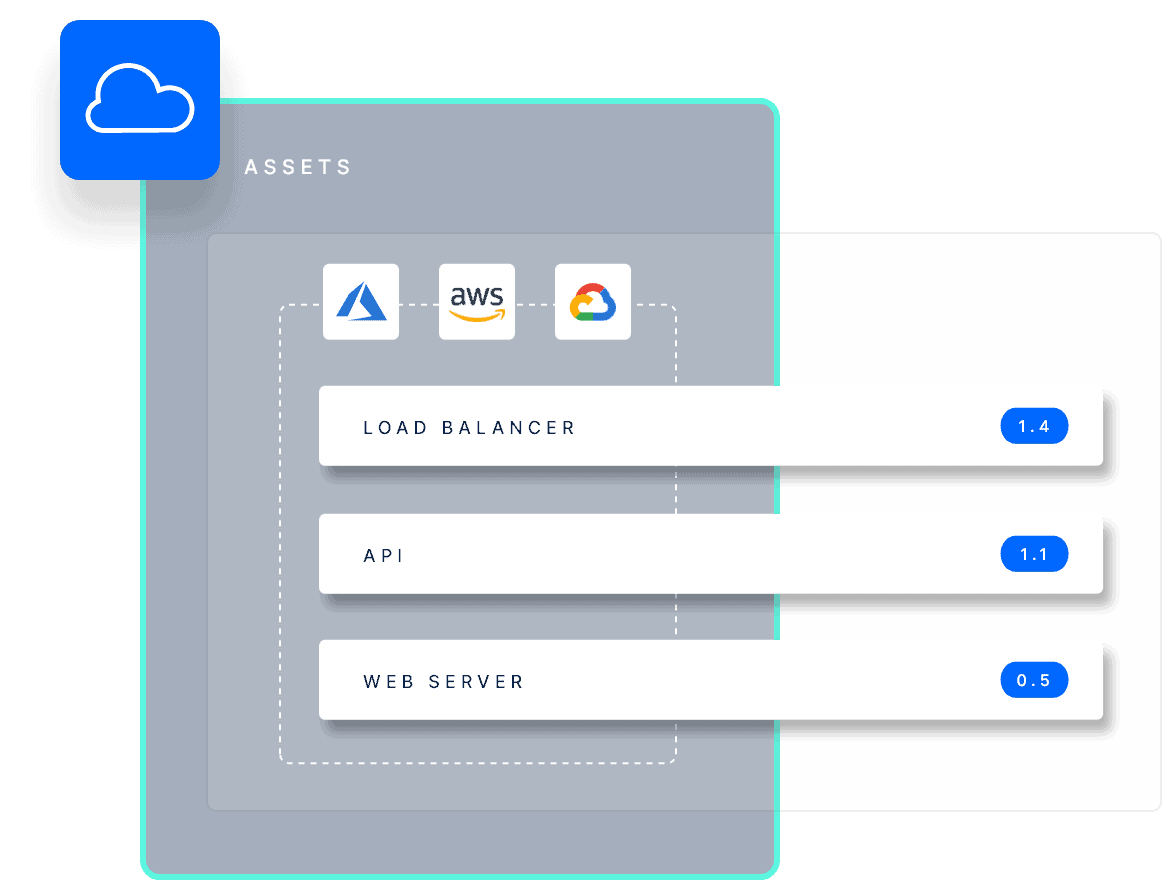
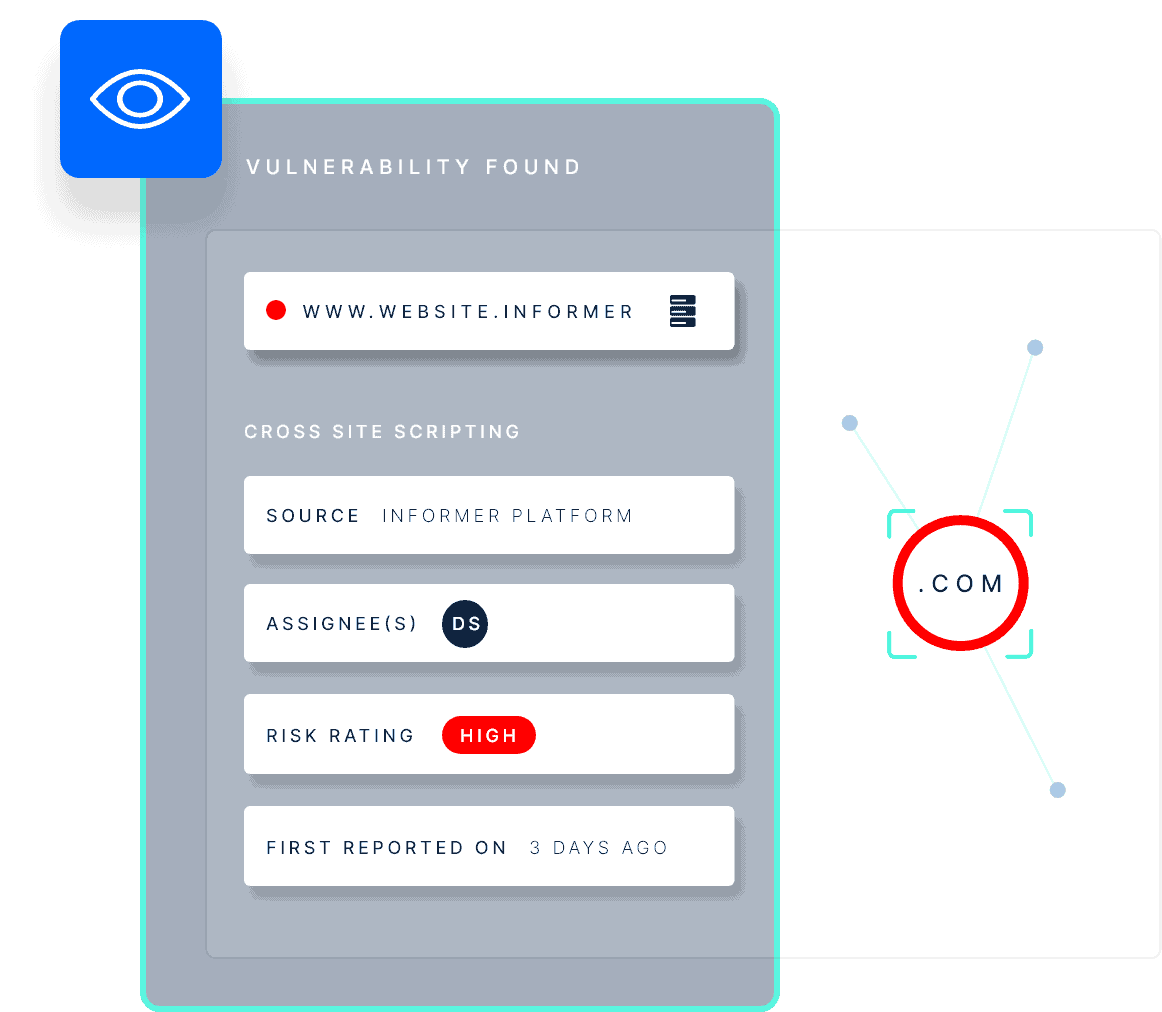
Gain Visibility of your Cloud Attack Surface
Low-cost data storage, spinning up computing infrastructure in seconds for app development, and users accessing valuable SaaS applications – the many use cases for cloud services influence its widespread adoption. However, what is often overlooked is how increasing the number of assets shared and stored in the cloud can broaden an organization’s attack surface. To ensure the security of cloud infrastructure and applications, IT and security teams need complete visibility.
Manually tracking cloud assets is a hugely time-consuming and inefficient task. With so many moving parts in modern cloud ecosystems, it’s easy to miss something crucial, such as an open storage bucket containing sensitive data. This is where Informer’s automated cloud asset monitoring comes in, providing an accurate asset inventory that’s updated and mapped in real-time.
Utilizing cloud asset monitoring offers a comprehensive solution to security threats posed by the ever-increasing number of cloud assets. With its advanced capabilities, IT and security teams can easily track and monitor assets, ensuring complete visibility of their cloud infrastructure.
With automated cloud asset monitoring, IT and security teams can focus on other critical areas of their security program, knowing that their cloud assets are being monitored 24/7.