Asses the real risk of discovered vulnerabilities
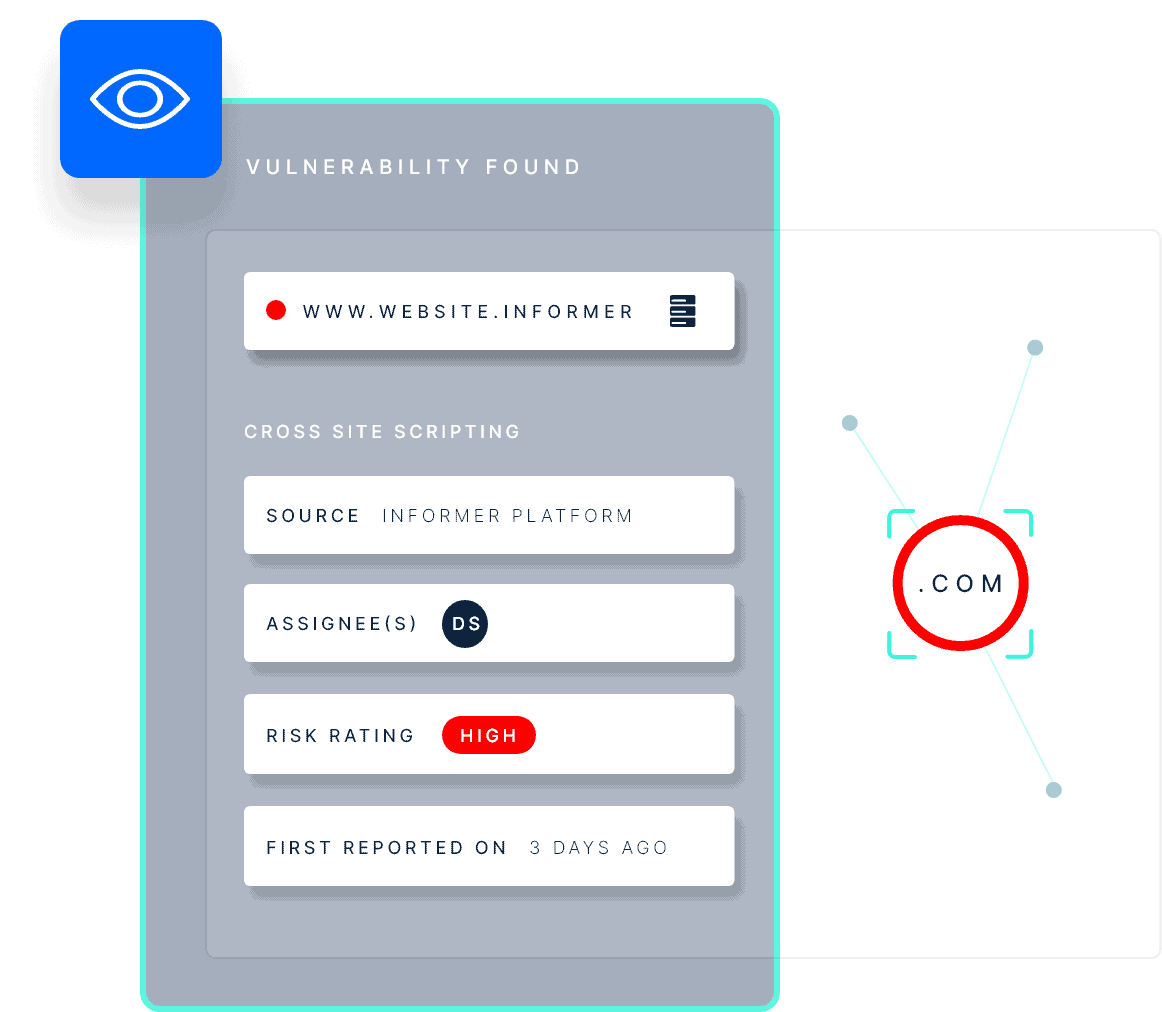
Vulnerability scanning excels at automating and scaling vulnerability discovery, and an accurate asset inventory is essential to ensure you have the coverage and accuracy required. But how do you assess the real risk of what’s discovered?
With a large and complex infrastructure composed of different servers, apps, and services, the business implications of a vulnerability can’t be fully captured by a single metric.
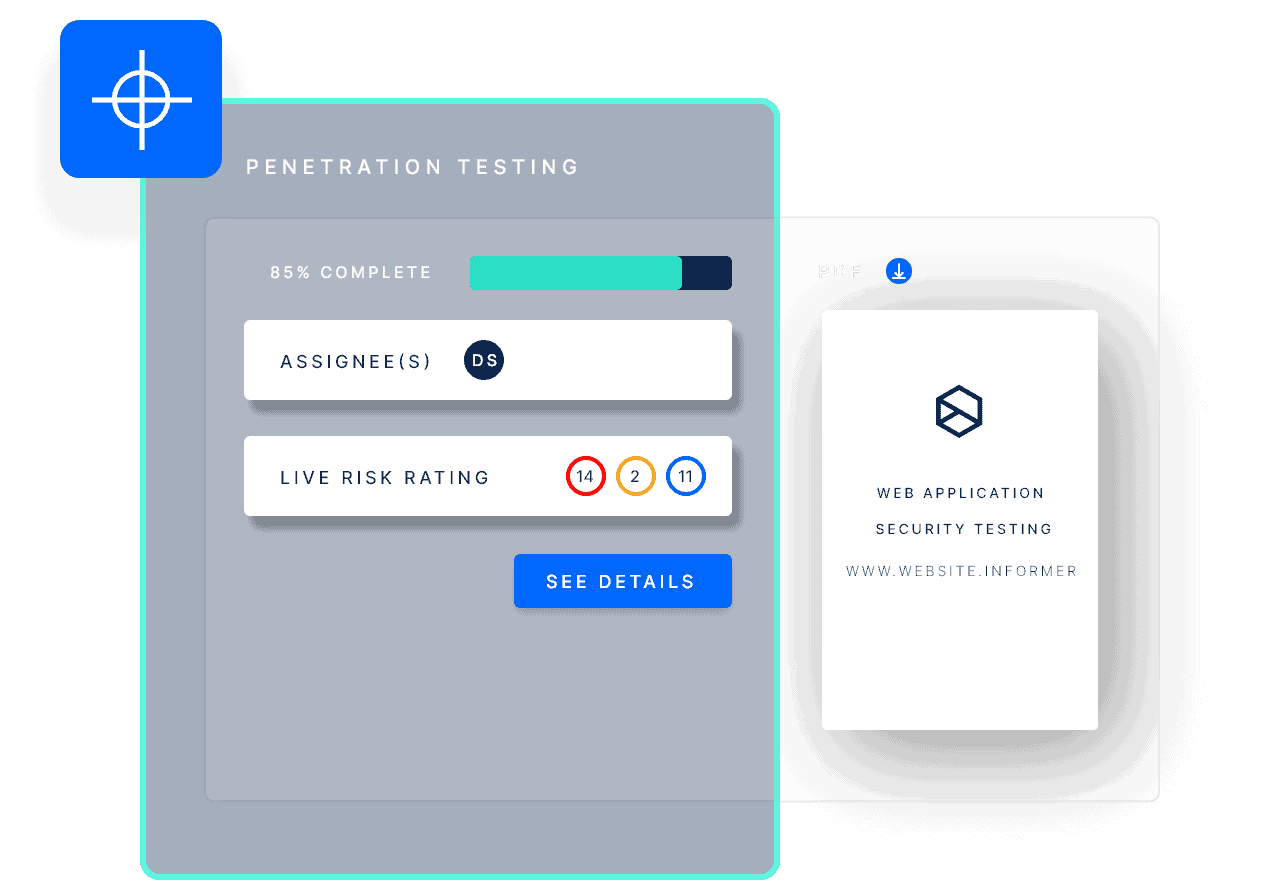
When combined with risk validation from expert pen testers, you get a much more precise indication of vulnerability severity. Complete risk validation focuses your mitigation efforts on vulnerabilities with the largest potential for destructive business impacts.