Discover, Identify, and Secure Your Internet-Facing Assets with EASM
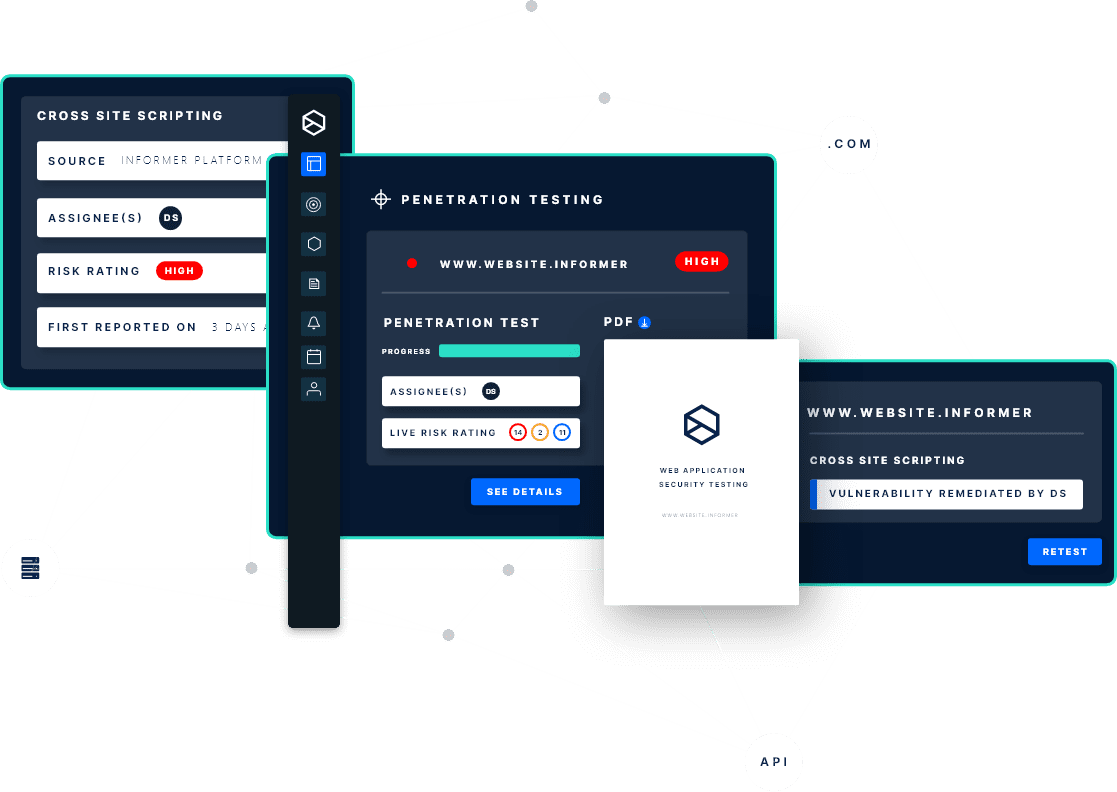
Uncover your external attack surface in seconds with our cutting-edge attack surface discovery engine. Our EASM platform uses active scanning and leverages hundreds of data sources to quickly and efficiently identify all of your digital assets, using just your seed domain as the starting point.
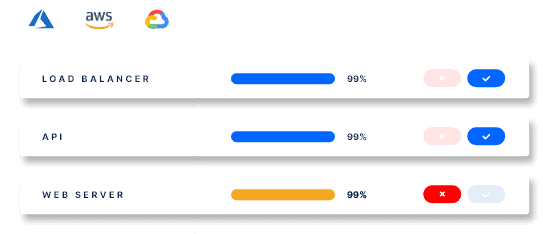
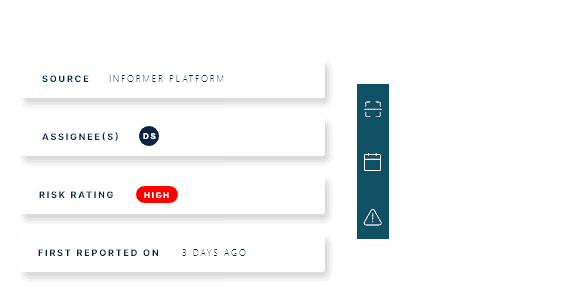
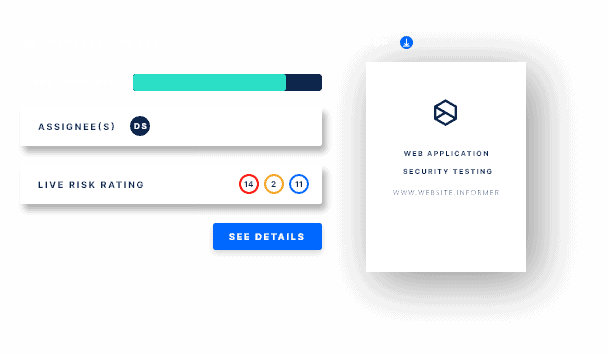
Our platform continuously discovers and scans your online environment, updating your asset inventory for a comprehensive view of your external attack surface. It identifies new or risky assets, collects and analyses real-time cyber intelligence data like vulnerabilities, misconfigurations, exposures, and threats during scanning. This provides valuable insights into your digital assets’ security posture, helping prioritize and remediate critical issues.
Asset Discovery