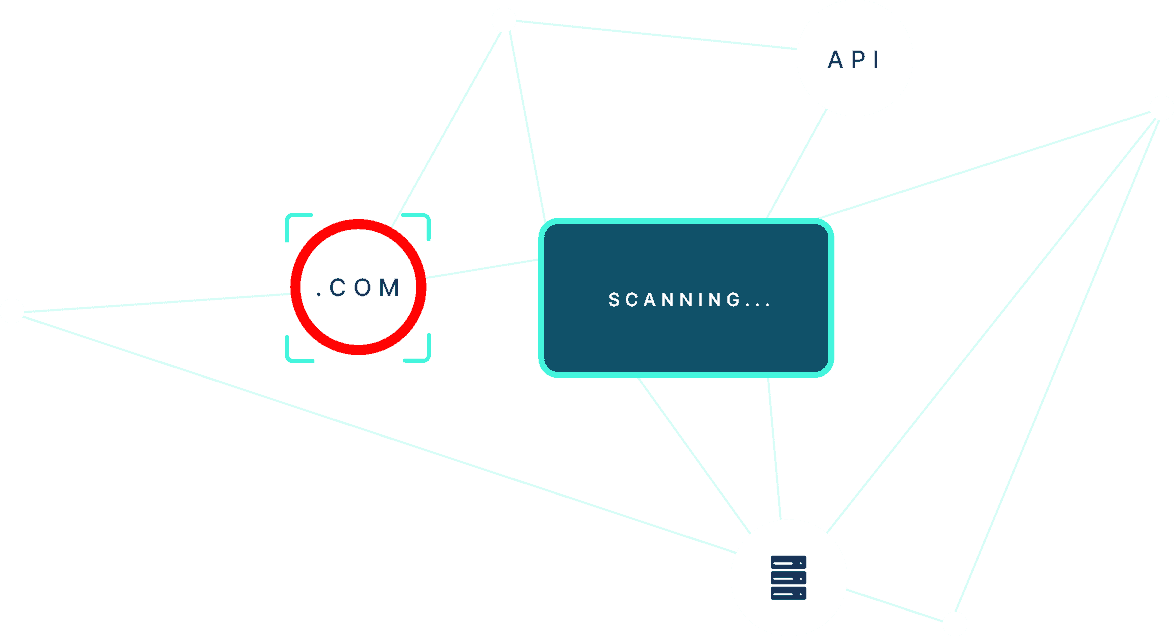
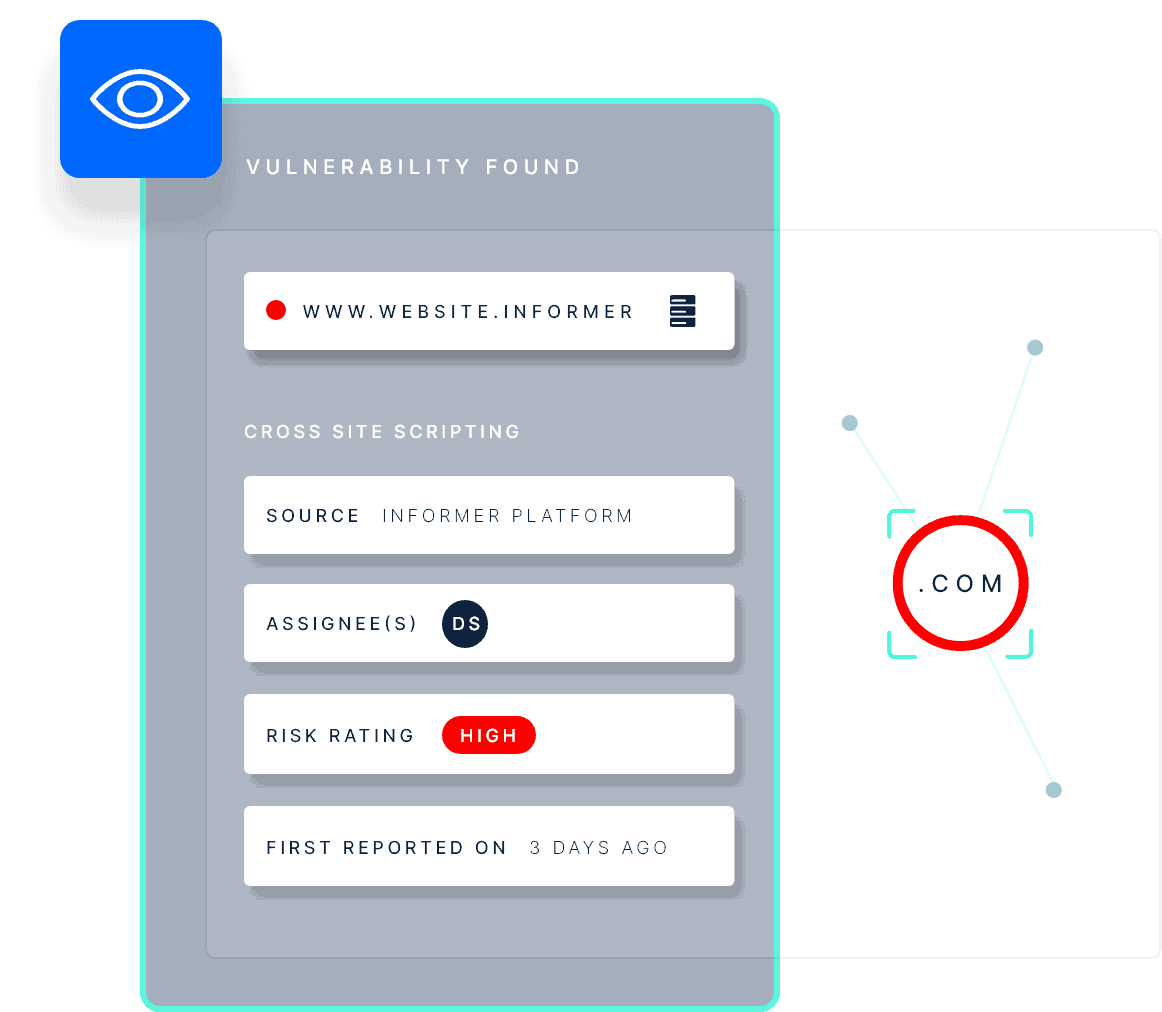
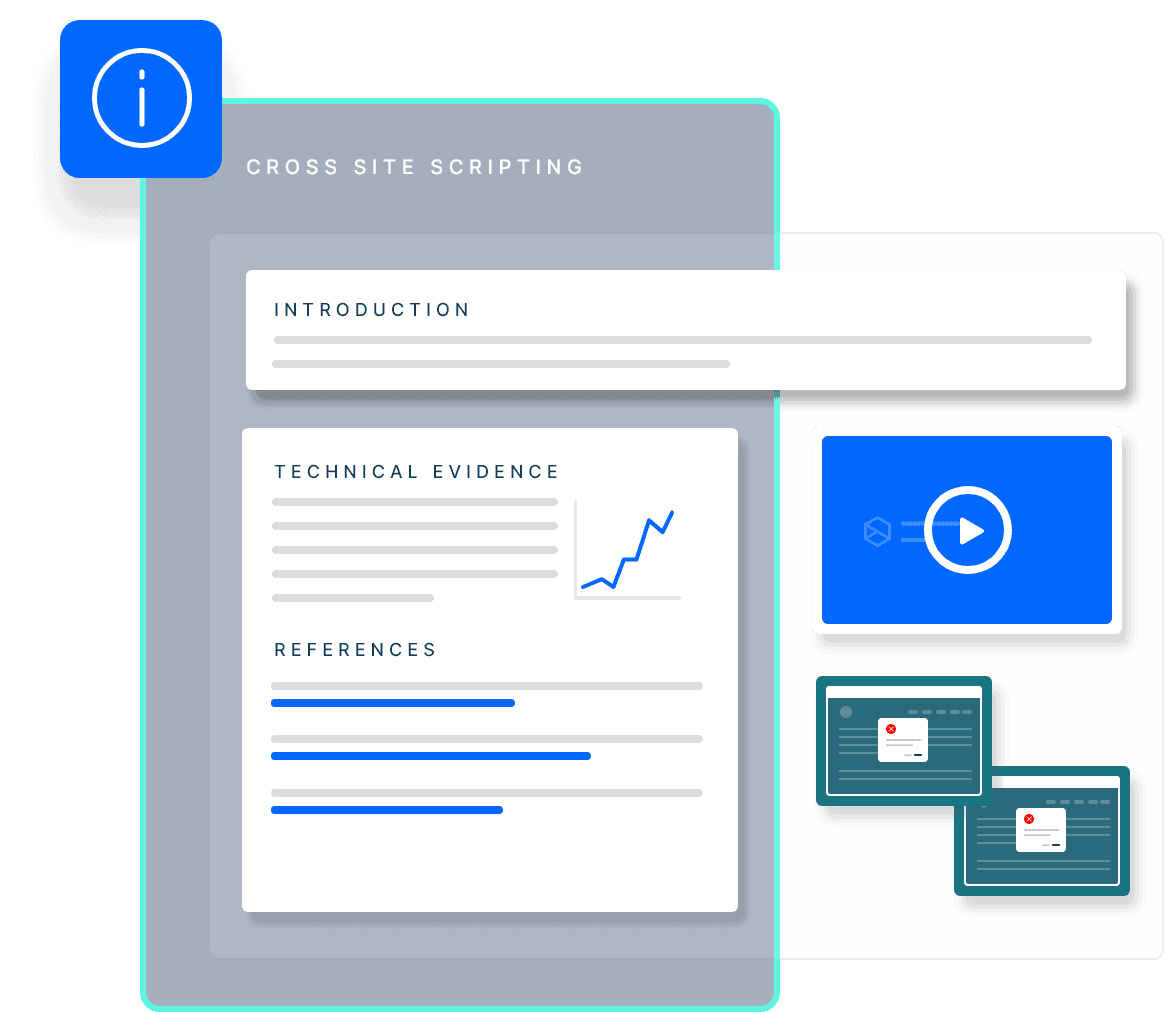
Vulnerability Discovery Helps You Secure Your Entire Attack Surface
Our vulnerability discovery module scans your entire external attack surface for vulnerabilities and exposures across applications, infrastructure and cloud environments. It helps you identify, prioritize, and remediate your assets’ most critical and exploitable weaknesses. It also alerts you when new threats are identified and provide actionable recommendations and guidance. Vulnerability discovery is part of a comprehensive attack surface management program that gives you an attacker’s view of your external and internal exposure.