Last Updated on 4 August 2023 by Elise Imison
In this comprehensive guide, we will delve into the world of DMARC (Domain-based Message Authentication, Reporting, and Conformance) and explore how it enhances email security, protects against phishing attacks, and ensures the authenticity of emails. As a leading expert in cybersecurity, we will provide you with valuable insights and detailed information on how DMARC works, its benefits, implementation steps, and best practices.
What this article covers
What is DMARC?
DMARC, an abbreviation for Domain-based Message Authentication, Reporting, and Conformance, is an email authentication protocol designed to prevent email spoofing and phishing attempts.
By enabling organizations to set policies that validate the authenticity of incoming emails, DMARC ensures that only legitimate emails are delivered to recipients, reducing the risk of cyber threats and data breaches.
How DMARC Works
The DMARC process involves three key components: SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), alongside the configuration and reporting abilities of DMARC itself.
SPF: Sender Policy Framework
SPF allows you to specify the email servers that are authorized to send emails on behalf of your domain.
These rules are defined within an ‘SPF record’ which contain a list of authorised senders – the IP addresses of the outbound email servers for your organization. An SPF record is published to the Domain Name System (DNS) as a TXT record. Upon receiving mail, a recipient’s mail server can then check the SPF rules published within the sending domain’s DNS records to verify if the email is originating from an authorised server.
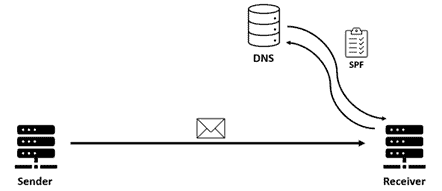
By doing so, organizations can guard against email spoofing – where users are targeted by malicious emails with forged sender addresses impersonating the legitimate organization.
DKIM: DomainKeys Identified Mail
DKIM validates both the identity of the sender and the integrity of the email content. This is achieved by the outbound email server adding a digital signature to the email header which can be verified by the recipient.
The DKIM signature is created using a combination of hashing and encryption. The first step involves feeding the contents of the email (e.g the body, subject line, sender field etc.) into a hashing algorithm to produce a hash of the email contents. The second step involves encrypting this hash using the sender’s private key, which is known only to the sender. Importantly, data that is encrypted by the domain’s private key can only be decrypted by the corresponding public key. Like an SPF record, this public key is published as a TXT record to the Domain Name System. Now that the signature has been generated, it can be added to the email header.
On the recipient’s side, the signature will be decrypted by retrieving the sender’s public key from the domains DNS records. The recipient then uses the same hashing algorithm as the sender to generate another hash of the emails contents to verify whether the two hashes match.
This process can be summarized in the following steps:
- The sender generates a hash by feeding the contents of the email into a hashing algorithm.
- The hash is then encrypted by the sender’s private key to produce the resulting DKIM signature, which is added to the email header.
- The recipient retrieves the sender’s public key from the domain’s DNS records and uses this to decrypt the signature and retrieve the underlying hash.
- The recipient uses the same hashing algorithm to calculate another hash value based on the email contents. If this matches the decrypted hash value, the email will pass DKIM verification.
With DKIM in place, an attacker would be unable to generate a valid signature that would pass authentication as the only the legitimate domain owner holds the private key. Additionally, DKIM guards against the email being tampered with whilst in transit, as the modified email contents would not match the DKIM signature.
DMARC: Domain-based Message Authentication, Reporting and Conformance
DMARC works alongside SPF and DKIM to help recipient mail servers decide what action is to be taken when an email has not passed the checks performed by SPF and DKIM. DMARC also provides reporting abilities so that you can measure the impact this is having on email deliverability.
DMARC is configured using a set of tags. As with SPF and DKIM – DMARC configuration is added to the TXT record in DNS. The required tags are summarized below:
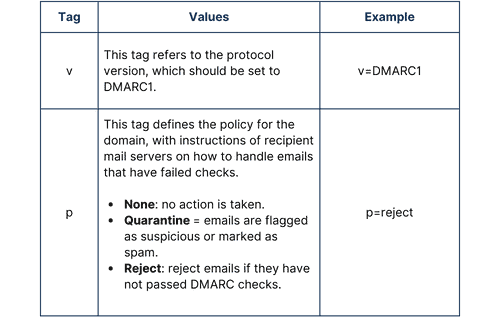
To enable reporting, you may also wish to define the following tags:
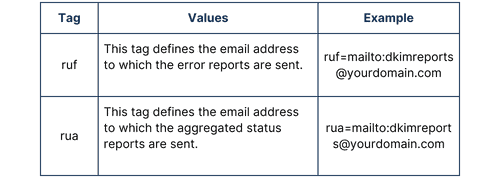
When first implementing DMARC, it is recommended to set the policy tag to none, alongside specifying an email address to send aggregated reports to via the rua tag. A policy will not be enforced but you will receive daily reports providing details on the number of emails which have passed or failed. You can then fine-tune your DMARC configuration to ensure that emails aren’t unintentionally quarantine or rejected prior to enforcing a policy.
An example first DMARC record may be;
v=DMARC1; p=none; rua=mailto:dmarcreports@yourdomain.com
Best Practices for Successful DMARC Implementation
To maximize the benefits of DMARC and ensure a smooth implementation process, follow these best practices:
Start with a Soft Rollout
Begin with a “none” policy to collect data without impacting legitimate emails. Use the reports to identify and resolve any issues before moving to a stricter policy.
Regularly Review DMARC Reports
Frequently analyze DMARC reports to identify trends, potential threats, and areas for improvement. Adjust your DMARC policy accordingly to enhance email security.
Maintain Up-to-Date SPF and DKIM Records
Ensure that your SPF and DKIM records are always current and accurate. Periodically review and update them as your email infrastructure evolves.
Educate Employees and Users
Raise awareness among your employees and users about DMARC and its benefits. Train them to recognize phishing attempts and report suspicious emails promptly.
Final thoughts
In conclusion, DMARC is a powerful email authentication protocol that enhances email security, protects against phishing attacks, and preserves the authenticity of emails. By implementing DMARC and following best practices, organizations can significantly reduce the risk of cyber threats emanating from email attack vectors and protect their brand reputation. Remember to monitor DMARC reports regularly, and gradually enforce your DMARC policy for optimal results.
Remember, strong email security is vital and DMARC serves as a robust defense against cybercriminals seeking to exploit vulnerabilities. Secure your domain and emails with DMARC today to ensure safer communications and build trust with your recipients.
Frequently Asked Questions
What is the primary purpose of DMARC?
DMARC’s primary purpose is to prevent email phishing and spoofing by allowing senders to specify how their messages should be handled by receiving mail servers.
How does DMARC enhance email deliverability?
DMARC enhances email deliverability by ensuring legitimate emails reach the recipient’s inbox while unauthorized messages are rejected or sent to spam folders.
Is DMARC compatible with regulatory compliance standards?
Yes, DMARC can align with various regulatory frameworks, such as GDPR and HIPAA, to meet industry-specific email security requirements.
Can DMARC completely eliminate phishing attempts?
While DMARC significantly reduces phishing attempts, it may not completely eliminate them. However, it serves as a strong line of defense against email fraud.
What are some common challenges in DMARC adoption?
Common challenges in DMARC adoption include misconfigured SPF and DKIM records, lack of understanding of DMARC reports, and handling false-positive results.
How does DMARC contribute to brand reputation protection?
By preventing email phishing and impersonation, DMARC ensures that your brand’s reputation remains intact, as recipients trust the legitimacy of your emails.