Last Updated on 31 March 2023 by admin
Zerologon (CVE-2020-1472) is a critical vulnerability that affects Windows servers. Given certain circumstances, this vulnerability can allow an attacker to bypass authentication and then gain administrator-level privileges in a matter of seconds.
This vulnerability received the maximum score of 10 under the Common Vulnerability Scoring System (CVSS) and has led Microsoft to strongly advocate the installation of the security patches released in August 2020 on all Active Directory domain controllers.
What is Active Directory?
Zerologon affects the Active Directory resource found typically on Windows enterprise servers. The severity of this vulnerability was scored so highly because Active Directory contains and maintains the security policies and permissions of all users for the entire network. These security policies and permissions can range from blocking users from changing the background of their computers to granting users the ability to read highly sensitive documents. Depending on the size of the enterprise network, this could affect hundreds of thousands of users throughout the entirety of the company’s domain.
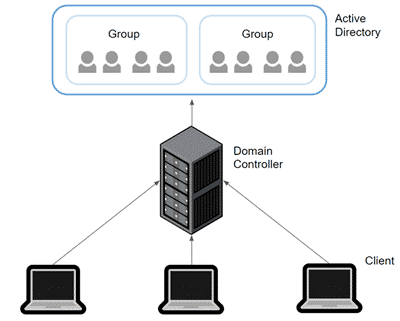
Active Directory can essentially be considered as a method of Single Sign-On. Once a user has successfully authenticated themselves, with a username and password, they are allowed to access all of the resources or services that they have permission to access, without needing to re-enter their credentials. In order for users to gain access to these resources and/or services, they must first be able to connect and provide their valid credentials to a server. This server is known as the domain controller.
How do domain controllers work?
The main server(s) in charge of Active Directory is named the domain controller. This server acts as the gateway between the user and the networks. Once a client’s computer has connected to the domain controller, the user will then be granted access to the network and all of its resources and services. However, before the user is granted access to the network, the domain controller requires the user to authenticate themselves. As a result, the domain controller plays a very crucial role in the network as it houses the database which contains all the passwords, user accounts, client computer information, etc. throughout the whole network. This makes domain controllers a high-value target during a cyber attack as it contains all information necessary for an attacker to cause major disruption throughout the entirety of the network.
An analogy to describe the relationship between Active Directory and domain controllers is the same relationship between an air traffic control tower and the flight schedule. The air traffic control tower, which is similar to a domain controller, is in complete control of what enters the airspace whereas the flight schedule is the database that contains all necessary information about when and where each flight is taking place.
Zerologon (CVE-2020-1472) vulnerability explained
Netlogon Remote Protocol
Zerologon is a vulnerability that is able to bypass authentication when a user connects to the domain controller. When a user connects to the domain controller, a process called the Netlogon Remote Protocol is used to help identify and authenticate users and client computers before they are granted access to the network. The main purpose of this process is to help domain controllers identify, authenticate, and facilitate the many thousands of users logging into the server.
Like other processes that are associated with login functionality, the Netlogon contains a feature that allows users to update their passwords. This feature in general is a convenient feature since it allows system administrators to change passwords for users who have forgotten their credentials. However, this functionality plays a key role in how the Zerologon vulnerability works and how it can be so lethal. Although this is only one aspect of why this vulnerability is so dangerous, the second aspect is due to the encryption that is implemented.
Insecure encryption
Netlogon Remote Protocol is a service that can be considered to be part of the Remote Procedure Call services. These services typically follow the same methods of encryption for authentication however, Netlogon is unique in the fact that it does not use the same implementation of encryption for authentication compared to the other services. As a result, this vulnerability is only unique to the NetLogon function and does not affect other remote procedure call services.
What makes Zerlogon dangerous is the ability to take advantage of the way that encryption was used throughout authentication. It was discovered by Tom Tervoort, a security researcher from Secura, that the way that the encryption method (AES-CFB8) was implemented contained a fatal flaw. Successful exploitation of this encryption method ultimately bypasses any cryptography that is used during the Netlogon function and undermines all authentication. As a result, an attacker is able to gain access to the network by successfully impersonating a valid user, and therefore granted access, despite not having the correct credentials.
Compromising the server
To gain access to the internal network, an attacker can bypass authentication by tricking the domain controller by impersonating as a valid user without knowing the credentials of the user. The attacker is able to trick the domain controller because of the flaw in the encryption that was insecurely implemented during authentication. Once an attacker has been able to impersonate another user, the attacker is able to change the user’s password to any password of the attacker’s choice or even have a blank password.
What makes Zerologon so dangerous is its ability to impersonate as the domain controller itself and once authenticated, its ability to change the domain controller’s password. Ultimately, an attacker that is able to control the domain controller gains administrative access and therefore is able to fully control the network with access to any service or resource.
In order to impersonate another user, the Zerologon attack exploits the NetLogon function. This attack affects the communication between the user’s computer and the server (domain controller). When the computer and the server communicate, numerous requests are sent back and forth between each other to adequately validate that the computer is a verified user. These requests contain sensitive information that both the computer and the server can use to validate that they are who they say they. Since the requests contain sensitive information, they are encrypted to ensure no one can intercept the requests and read the information.
However, due to the flaw in the way that the encryption is used, if an attacker were to modify their request to just contain zeros in certain fields, it would cause the encryption to return a value that the server accepts and successfully validates regardless of whether the correct credentials were supplied.
It was discovered that if enough requests (on average 256) were made containing these fields of 0s, the server would successfully validate one of the requests despite the lack of valid credentials. After being authenticated, the attacker has the ability to change the password of any computer account or the domain controller itself.
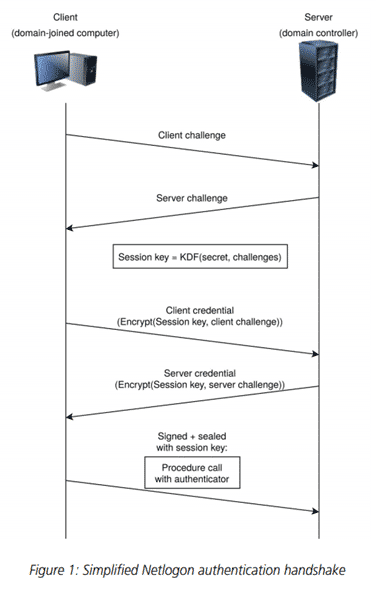
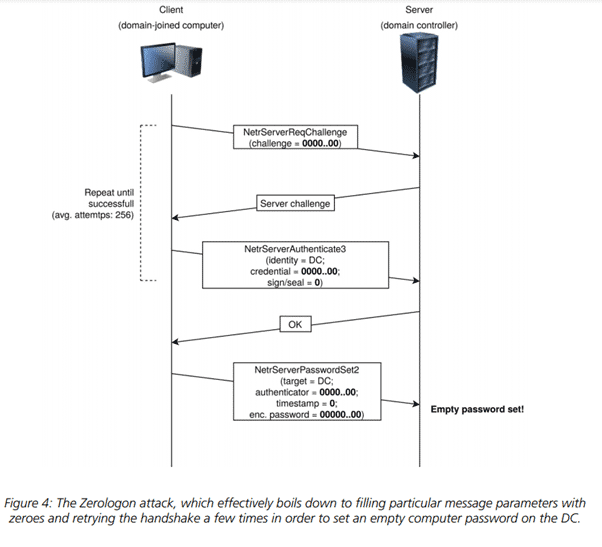
Image: Secura Zerologon Whitepaper [1]
An important note to mention is that this vulnerability does not allow attackers to break into Windows networks. The vulnerability is only possible if the attacker possesses the ability to connect to the domain controller in the first place. This vulnerability can be considered to be an insider attacker or more formally, a privilege escalation vulnerability. Privilege escalation vulnerabilities are vulnerabilities that enable an attacker to gain access to other users on the network with either the same level or higher level of access control.
Conclusion
The Zerologon is a critical vulnerability that can have drastic effects on a Windows server by potentially enabling an attacker to completely compromise the server. Even without the need for any user credentials, an attacker is able to obtain admin-level privileges/access and therefore control any asset or service in the entire network.
A patch was released in August 2020 to address this problem and a future patch has been planned for February of 2021. With the new patches, the Zerologon attack as previously described should no longer pose a critical threat and is now considered by Microsoft to be considered Exploitation Less Likely[2]. Indicating that this is a strongly recommended if not vital patch that should be implemented immediately.
References
[1] – https://www.secura.com
[2] – https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2020-1472